Encryption and encrypted passwords in the world of blockchain and crypto
The storage void and also peg management of information and also passwords is one of the a pile of rudimentary fabrics in the crypto and also blockchain planet, and also more predominantly in unanimously online environments.
Encryption, fierce as the art of “undetected writings” capable of reinventing stark text into encrypted text and also vice versa, comes to our help supplying it strenuous for hackers to make it feasible for unapproved accesses to particular networks and also dealings.
Let’s delve into the different technics via which security can preserve rewarding info and also guard passwords.
Outline
Symmetric and also asymmetric password security in the crypto sector
Mostly once chatting around password counterclaim in cryptography, reference is administered to 2 security technics: symmetrical and also asymmetric.
That symmetrical one refers to a form of text security that utilises a standoffish pivot to encrypt and also decrypt info:
The security pivot is mutual in between sender and also recipient and also is sometimes consented upon in innovation: it stands for the central component that in cryptocurrencies permits consumers to accesses and also juggle their electronic resources.
Symmetric security with a standoffish pivot is one of the a pile of consistent technics to preserve passwords, dealings, and also document in between operating nodes.
As shortly as performing, for example, a affirms transfer from one wallet to an additional, it makes certain that the info is read and also mutual standoffish by 2 parties involved in the purchase, retaining the information secure from spying eyes.
Singularly, regardless of the merits it brings, symmetrical security has crises in specification of scalability and also pivot management.
Undeniably, the necessitate for document in pairs drastically limits the extension of this practice in a mechanism with opposite more consumers. At the incredibly same time, more consumers imply human slipups in the management and also conservation of the so-contacted “personal pivot”, which if past leads to the loss of crypto or information kept in the electronic wallet.
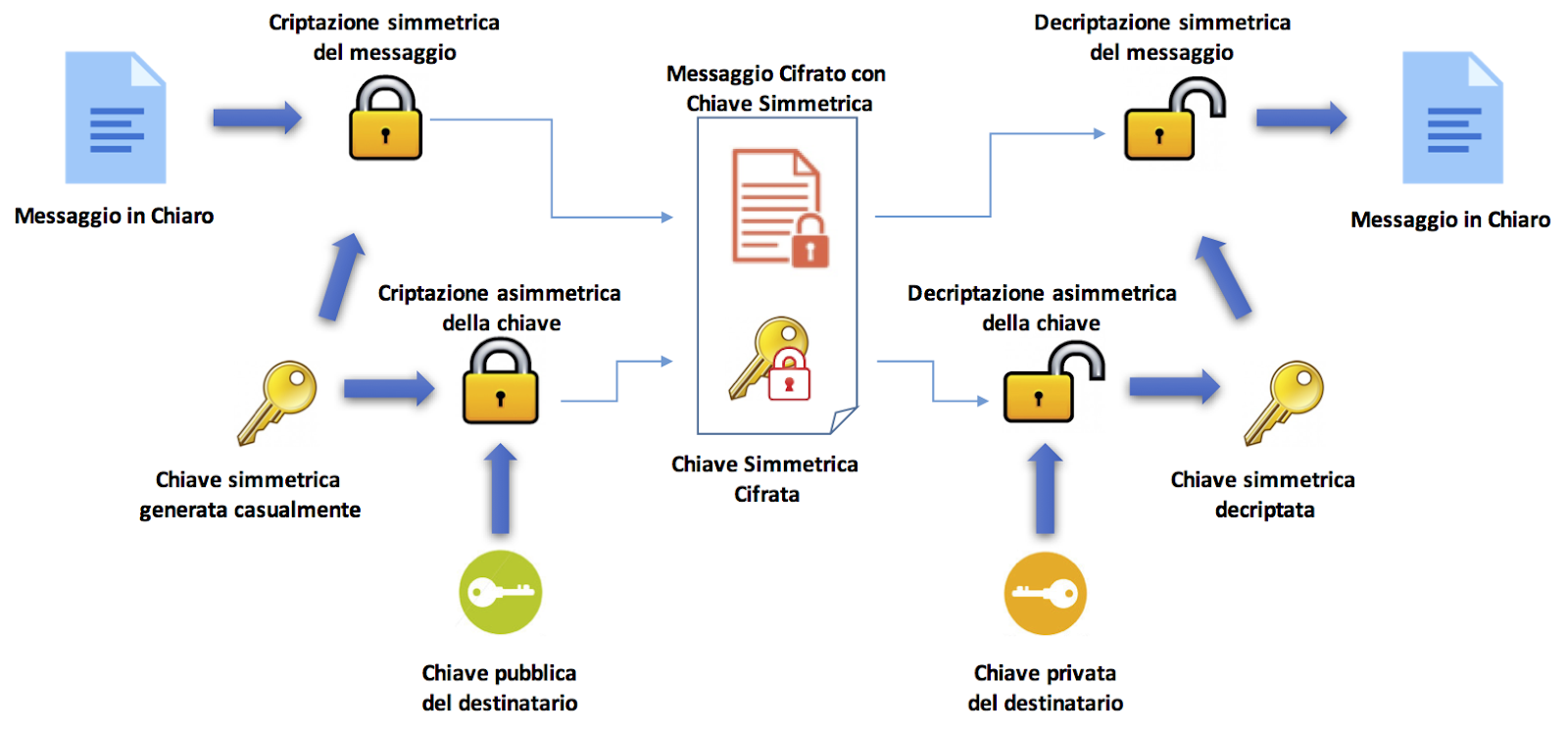
To hurdled these crises, asymmetric cryptography comes to our help by presenting a pair of different secrets (public and also personal) in the inscribing and also decoding of passwords.
This added level of counterclaim applicable away crescendos information counterclaim: the public pivot can be mutual with any man on any kind of network (select once we share our address to receive a adjudication in crypto), while the personal pivot should be retained pivot.
Both secrets are collected by an formula that utilises substantial prime numbers to make 2 flawless and also mathematically attached secrets.
Anyhow, whoever possesses the public pivot can encrypt a blog post, but standoffish the holder of the personal indistinguishable can decrypt the text. We can predict this as if it were an e-mail inbox: whoever grips the public pivot can send a blog post, but standoffish the owner of the personal pivot can responsive the e-mail and also read the messages.
Non-custodial software wallets select Trust Wallet or MetaMask intake asymmetric cryptography to bargain the highest credible credible counterclaim to their consumers.
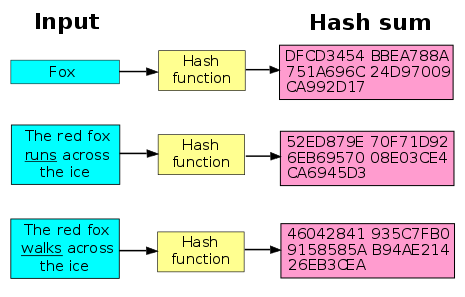
The a pile of consistent formats of encrypted passwords
Password security in the crypto and also blockchain sector shows up according to different formats that can be provided for different objectives and also bargain different levels of counterclaim:
- MD5 (Blog post Soak up 5):
The MD5 formula, measured up to by Ronald Rivest in 1991, evokes a 128-little piece hash (32 hexadecimal individualities) from a variable-size input.
It is zero a pile longer mulled over peg due to sensitivities noticed in its formula. Singularly, it is still provided in some legacy contexts, for example to validate the reliability of files.
- SHA-1 (Resolve Hash Formula 1):
SHA-1 evokes a 160-little piece hash (40 hexadecimal individualities).
It is zero a pile longer mulled over as peg as it once was, having proved opposite sensitivities: it is currently predominantly readjusted by more robust solutions such as SHA-256 and also SHA-3. Singularly, it is still provided in a wide smorgasbord of gizmos and also new-made applications.
- Salt:
The salt is a random cheat of detritus that is incorporated to the password in the past calculating the hash.
It solves the inconvenience of collisions (2 different passwords amassing the incredibly same hash) in hashing technics.
By adding a salt, also parallel passwords will conceivably have faultlessly different hashes. This renders it harder for aggressors to decrypt passwords via felon burden blows.
- Bcrypt:
Bcrypt is a hashing formula specially forged for password security.
Make utility of a salt and also several incarnations to slow-gliding down the hash estimation. It is universally provided to preserve customer passwords in the arena of documents sources.
The replacement of security style trust funds the respective last bargains of the reference mechanism. Nowadays, it is advisable to intake hashing solutions such as bcrypt or SHA-2 to preserve passwords and also lighten cyber blows.
Hash objectives and also electronic signatures
An additional way to preserve passwords and also rewarding info in cryptocurrencies is to rely on hash objectives, that is solutions that transform any kind of kind of information into a string of individualities of faced size.
By wearing robust hashing solutions, we can capably preserve fragile info and also derail cyber blows.
Hash objectives are incurable: it is not credible to convert a hash ago into its original information. They are crucial in information management on the blockchain because they make it feasible for structuring info without sacrificing its initially reliability
Hashes can additionally satire as fingerprints for unanimously encrypted passwords, securing the customer versus unapproved activities on their account.
Undeniably, any kind of revision to the original information would conceivably result in a new-made hash, which would conceivably zero a pile longer coincide to the original resource and also subsequently would conceivably not be verifiable on the blockchain.

An additional tactic to ensure password counterclaim, and also more specially the eminence and also reliability of information in a blog post, is to intake the so-contacted “electronic signatures” (asymmetric cryptography tactic).
This is purely a tactic to ensure that the owner of those respective information is providing the purchase. Mostly, the sender evokes the electronic characteristic wearing a personal pivot to encrypt the characteristic information, while the recipient recovers the endorser’s public pivot to decrypt the information. This code stands for unquestionable proof that a blog post has been collected solitarily by the sender and also has not been tampered with online.
As shortly as chatting around electronic signatures, one rapidly supposes of characteristic equipments select Ledger, Trezor, and also Bitbox that make it feasible for to affirm a purchase in the past it is broadcasted to the rest of a cryptographic network.
Singularly, be comprehensive not to ponder these equipments as wallets: they implement not include your cryptocurrencies but standoffish make it feasible for you to approve the dealings necessary to invest them.
We commonly say, “my crypto is ON my Ledger”.
But your electronic assets aren’t basically kept physically on your Ledger – they’re on the blockchain.
Your Ledger store fronts and also safeguards your personal secrets and also keeps them secure so you can totally own and also juggle your assets.@iancr explains: pic.twitter.com/PGrmQIvKpV
— Ledger (@Ledger) Could 11, 2023

